We're excited to announce the release of IPM version 0.10.0, a major update that introduces verified packages with comprehensive manifest generation for enhanced auditing capabilities. This release represents a significant step forward in package integrity, compliance, and operational transparency for enterprise infrastructure management.
Verified Packages: Enterprise-Grade Package Integrity
The flagship feature of version 0.10.0 is our new verified packages system, designed to provide unprecedented transparency and security for infrastructure packages. This feature addresses growing enterprise requirements for package provenance and content verification through cryptographic hashing and comprehensive manifest generation.
How Verified Packages Work
The verification process operates in two distinct phases:
1. Build Phase - Manifest Generation
When using the --include-manifest parameter during build, IPM generates a comprehensive manifest file that includes:
- Individual File Hashes: Each file in the package receives a cryptographic hash
- Complete Package Hash: The entire package content is hashed for overall integrity verification
- File Inventory: Complete list of all files included in the package
- Metadata Verification: Package structure and configuration details
ipm build --source ./my-package --destination ./build-output --include-manifest
Snippet of the manifest file:
{
"timeStamp": "2025-06-08T14:48:53.195792+00:00",
"hash": "SHA256:932bb7261627b147d9a8e4a41e282e9ccd07336399d41480e5623ef5d2459c06",
"totalFiles": 23,
"files": [
{
"path": "ipmhub.json",
"hash": "SHA256:30f7156cf6bcae721b3b572290e34f916f117c6d7681e9b9541f62d016138b9a"
},
{
"path": "main.tf",
"hash": "SHA256:11c0e73332a574b5cc312076a98b0b8ccba7e6d75e7816987322b0050bd6ca2f"
},
{
"path": "main.yaml",
"hash": "SHA256:d19f3be446b9707c3ae93305813b58cdf8b89eeed252b54ee8417392fd781c86"
},
{
"path": "README.md",
"hash": "SHA256:47ec043a6a898afc2a5a19d8e93fa34283b49c0134f6188ddda6567c6a411024"
}
}
2. Publish Phase - Integrity Verification
During publication, IPM automatically detects manifest files and performs comprehensive verification:
- File Presence Check: Verifies all files listed in the manifest are present
- Hash Validation: Confirms each file's current hash matches the build-time hash
- Content Integrity: Ensures no files have been added, removed, or modified since build
- Package Completeness: Validates the complete package hash against the manifest
Only packages that pass all verification checks receive the "verified" badge, providing cryptographic assurance that the published package exactly matches what was built.
Verification Benefits
Key capabilities include:
- Cryptographic Integrity: Mathematical proof that package contents haven't been tampered with
- Build-to-Publish Traceability: Guarantee that published packages match their build artifacts
- Supply Chain Security: Detection of unauthorized modifications between build and publish
- Compliance Assurance: Cryptographic evidence for audit and regulatory requirements
This two-phase approach ensures that verified packages provide enterprise-grade integrity guarantees, creating an unbreakable chain of trust from build to deployment.
Comprehensive Auditing with Summary Reports
IPM 0.10.0 introduces detailed summary reports for critical package operations, providing complete audit trails for compliance and governance requirements. These reports capture the full context of package operations, making them invaluable for enterprise environments with strict auditing requirements.
The new --summary-file parameter is available for:
- Export Operations: Complete record of package extraction and content verification
- Build Operations: Detailed build process documentation with included/excluded files
- Publish Operations: Comprehensive publication audit trail with verification steps
Example Usage
Generate a detailed audit report for any operation:
# Build with audit trail
ipm build --source ./my-package --destination ./build-output --summary-file ./audit/build-report.json
# Export with verification record
ipm export --package publisher/package-name --destination ./export-folder --summary-file ./audit/export-report.json
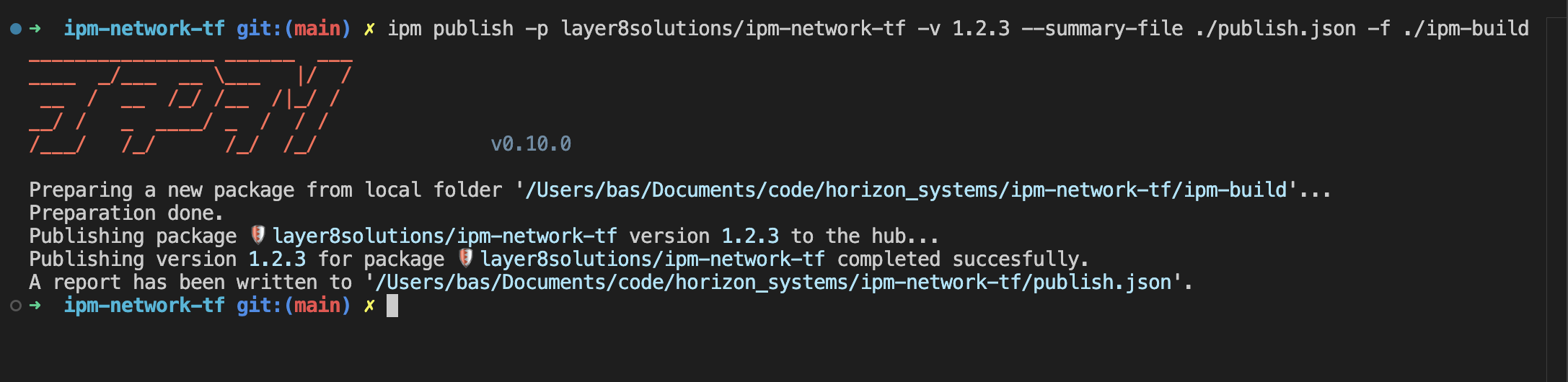
# Publish with complete audit trail
ipm publish --package publisher/package-name --version 1.0.0 --folder ./ --summary-file ./audit/publish-report.json
These reports provide the documentation needed for compliance audits, security reviews, and operational transparency that enterprise customers may require.
Enhanced Build System Intelligence
Version 0.10.0 significantly improves the build system with intelligent file and folder exclusion, resulting in cleaner, more efficient packages while maintaining security best practices.
Expanded File Exclusions
The build system now automatically excludes a comprehensive set of temporary and system files:
New File Extensions:
- .userosscache, .DS_Store, .Thumbs.db - System cache and thumbnail files
- .log, .pyc, .pyo - Logging and Python bytecode files
- .ps1xml, .psc1 - PowerShell configuration files
- .class, .o, .obj - Compiled object files
- .dll, .exe, .so, .dylib - Binary executables and libraries
- .iso, .trace, .pid - System and debugging artifacts
Intelligent Folder Exclusions
Enhanced folder exclusion logic automatically removes build artifacts and dependency directories:
New Folder Exclusions:
- bin - Binary output directories
- __pycache__ - Python cache directories
- .egg, .egg-info, .whl - Python package metadata
Default Behavior Changes
- Empty Folder Handling: Empty directories are no longer included in packages by default, resulting in cleaner package structures
- Workspace Exclusion: Fixed issues with workspace folder exclusion during build processes
- Consistency Improvements: Resolved edge cases where excluded items were incorrectly included
Enhanced Export Flexibility
The export command now includes a --force parameter for greater operational flexibility:
ipm export --package publisher/package-name --destination ./existing-folder --force
This allows exports into non-empty directories, providing more flexibility for integration workflows and development environments.
Improved User Experience
Version 0.10.0 includes several user experience enhancements:
- Refined Dry-Run Output: The
build --dry-runcommand now provides more intuitive, sorted output for better review - Polished CLI Output: Improved formatting and clarity across multiple commands
- Better Error Handling: Enhanced error messages and guidance for common scenarios
Implementation and Upgrade
Teams and Enterprise customers can access the new functionality immediately by upgrading to IPM 0.10.0. The latest version is available through:
- Winget (Windows)
- Brew (MacOS)
- Direct download from our website
Backward Compatibility
All existing functionality remains fully compatible. Verified packages and summary reports are opt-in features that enhance existing workflows without disrupting current operations.
Documentation and Support
Comprehensive documentation, including detailed examples for verified packages and audit reporting, is available at https://docs.ipmhub.io.
Looking Ahead
IPM 0.10.0 represents a significant milestone in our commitment to enterprise-grade infrastructure package management. The verified packages system and comprehensive auditing capabilities provide the foundation for advanced security and compliance features planned for future releases.
About IPMHub
IPMHub provides package management solutions designed to streamline Infrastructure as Code (IaC) distribution. Our platform helps teams maintain consistency and efficiency in their infrastructure deployments through features like Tracked Workspaces, verified packages, and comprehensive audit trails.
